Project Overview
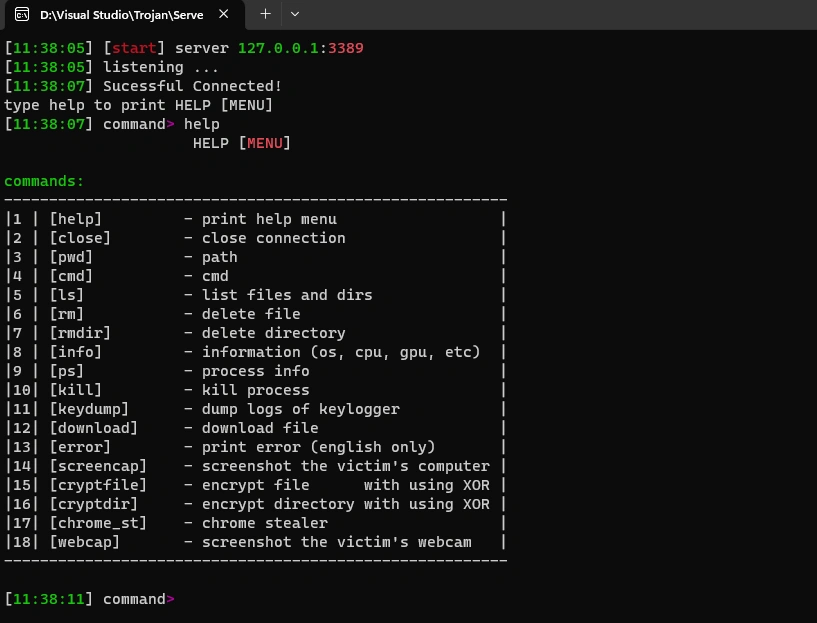
This C++ application is a Trojan horse, a type of malicious software that disguises itself as legitimate software to gain access to a user's system. Once executed, it can perform actions such as remote control, file manipulation, and data collection. This project builds upon concepts explored in other educational malware projects, including MBR viruses, ransomware simulations, and Blue Screen of Death (BSoD) demonstrations, to provide a broader understanding of system-level threats.
Functionality
Upon execution, the Trojan horse conceals the console window to evade detection and establishes a connection to a remote server or command center to receive commands. It can manage files, log keystrokes, take screenshots, and extract sensitive browser data. These features highlight core techniques also present in MBR or ransomware projects, showing how malicious software can manipulate system processes and data.
Educational Purpose
This project is intended strictly for educational purposes, to demonstrate the capabilities and risks of malicious software. It should be used responsibly in a controlled environment with explicit permission to test and analyze. Combined with prior experiments such as ransomware simulations and BSoD projects, it offers a comprehensive view of malware behavior and system exploitation techniques.