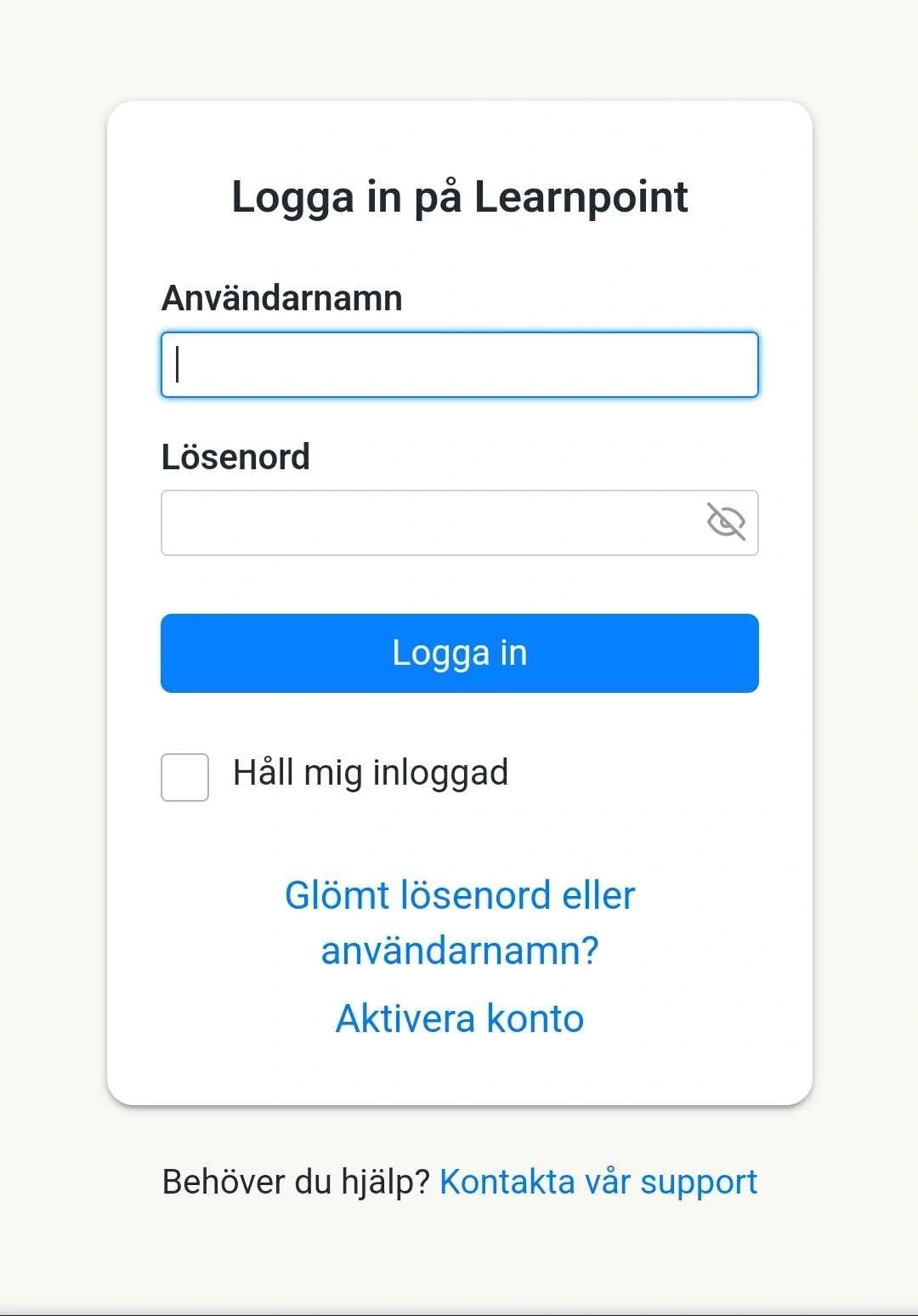
Authentic page — consistent fonts, expected layout and UI elements.
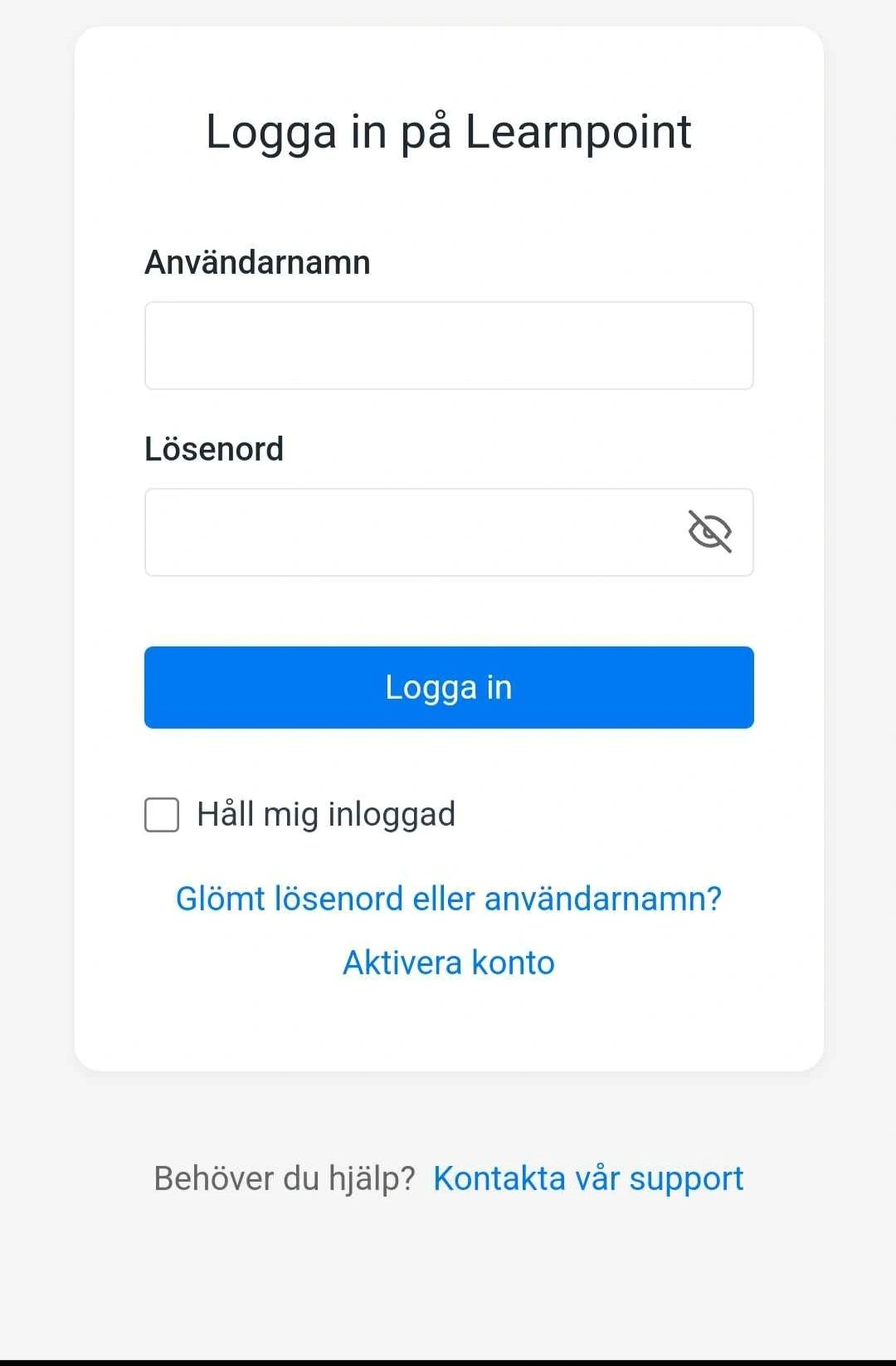
Subtle differences: slightly different font weight on the password field, small layout inconsistencies and unusual spacing — visual clues to check.
Project Overview
This C++ application demonstrates a phishing attack using an ESP32 device. The ESP32 can create a rogue access point and redirect connected users to a counterfeit login page that mimics a real site. The fake page captures credentials entered by users.
Functionality
When users attempt to log in, they may see a fake "processing" screen while their credentials are silently captured by the device. The demo is intended to show how attackers exploit trust and visual similarity to trick users.
What to Look For
Visible signs that a login page may be fake include inconsistent fonts, slight alignment or spacing differences, misspelled text, missing SSL padlock/invalid certificate indicators, unusual domain names, or unexpected form behavior. Always verify the URL and certificate before entering credentials.
Educational Purpose
This project is strictly for educational use to raise awareness about phishing risks. Use it only in controlled environments with permission for testing and training.